The High Price of Poor OPSEC: Inside the r1z Initial Access Broker Case
The r1z case shows how initial access brokers monetize firewall exploits and enterprise access at scale, while the actor’s OPSEC failures leave long-term attribution trails that expose the ransomware supply chain.
Updated January 21, 2026

Cybercriminals often leave trails that can unravel entire operations. One case recently highlighted the power of tracking online activity across multiple forums. Law enforcement monitored interactions, uncovering patterns and connections over time.
Investigators pieced together digital footprints that exposed real-world identities. This case shows how persistence and careful observation can bring hidden activity to light.
» Get started for free with KELA and strengthen your cybersecurity
Who Is r1z? An Initial Access Broker Selling Enterprise Network Access
An undercover FBI agent engaged him directly, purchasing compromised network access and advanced malware capable of disabling multiple endpoint detection and EDR products, allowing investigators to observe his operations from the inside.
That interaction ultimately enabled law enforcement to attribute the "r1z" persona to Albashiti, link his infrastructure to a major ransomware attack, and build a criminal case. Albashiti was extradited to the U.S. and pleaded guilty to selling access to at least 50 companies.
» Learn more about how ransomware operators gain access
r1z Cybercrime Activity Across Forums: Access Sales, Exploits, and Malware
KELA’s data identifies approximately 1,600 posts attributed to this actor across multiple forums, including XSS, Nulled, Altenen, RaidForums, BlackHatWorld and Exploit. His last known message was posted on XSS in December 2023 and discussed a cracked version of Cobalt Strike. He was also observed selling access to SonicVPN and to compromised companies across the USA, Europe, Mexico, and other regions, with many offerings involving RCE-level access.
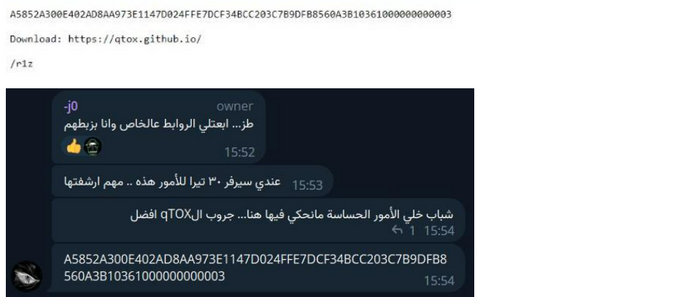
In addition, several posts were written in Russian, including activity on forums of Russian origin. Across his activity, the actor was seen selling an EDR killer (likely the same tool advertised as effective against FBI environments) and shared TOX contact details for follow-up communication.
» Learn how to reduce damage from info-stealing malware
OSINT and Attribution Signals Linked to the r1z Threat Actor
KELA has been tracking this actor since 2022 and was able to obtain additional identity-related information in near real time. Leveraging KELA’s data lake sources to uncover additional information about r1z, a search for his username yielded several results, revealing accounts on:
- RaidForums
- Nulled
- Doxbin
- CrackedTo
- Altenen
These were associated with two email addresses: gits.systems@gmail.com and cobaltstrike@tutanota.com.
While the Tutanota email appears to be a more temporary email that r1z used, analysis of the first email address revealed its presence in at least 30 compromised databases. These leaks contained associated passwords, phone numbers, additional usernames, birthdate, and IP addresses linked to non VPN, standard ISP providers based in Jordan. The Gmail address was also listed as the contact for the company named “OrientalSecurity” in Amman, alongside Firas full name and phone number. Some listed Facebook posts regarding hiring for the company were also found.
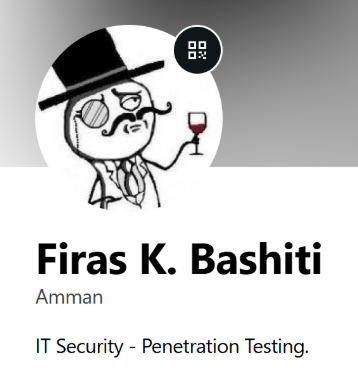
In one data leak, a Gravatar account was found to be registered under his personal name – Firas K. Bashiti, with the title as “IT Security – Penetration Testing”. This account also featured the same profile picture used by his r1z moniker in multiple forums. Usernames that were found in other leaks included OrientalSecurity, j0rd4n14n, bashiti, j0, f1r4s and Eddy_BAck0o – as some of these were found on his other profiles mentioned in this blog, like j0rd4n14n.
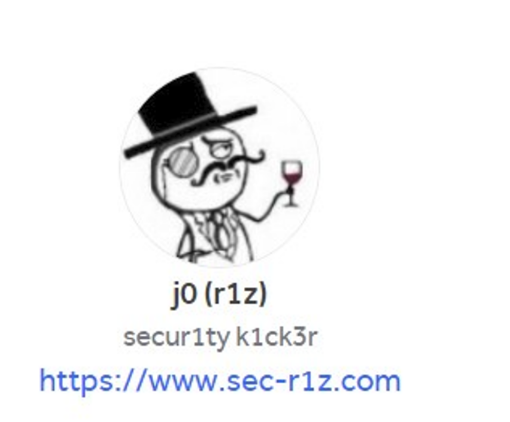
The actor also operated a Telegram channel (@secr1z), where he shared a TOX address that matched the one published in his forum posts. Approximately two years ago, KELA attempted to contact him on Telegram (@j0rd4n14n), but he denied being the user, stating that people frequently contacted him by mistake and that he intended to change the username. Minutes later, he updated both his profile photo and username to -j0 and deleted the conversation.
Despite this denial, the TOX ID, which is unique to each user, enabled KELA to confidently link the actor operating under the r1z alias with the Telegram account. Further corroboration was found on his website (sec-r1z.com), which was promoted through the Telegram channel, where a file titled "join.txt", listed the same TOX address.
The actor’s website, sec-r1z.com, was created in 2009, and based on WHOIS information, also reveals personal details of Firas, including the same Gmail address, alongside additional details like address and phone number. Based on archives, this website had a few variations, but was once an Arabic-speaking forum for cyber. Based on the Gmail address, the actor has registered at least 60 websites, most of them were related to the IT field and Jordan. Moreover, the vast majority of these websites were registered with a company called ENOM.
Reviewing Firas’s social media presence led to several additional findings. Photos used across different profiles were identical to the profile image associated with his forum activity under the alias r1z, directly linking the accounts.
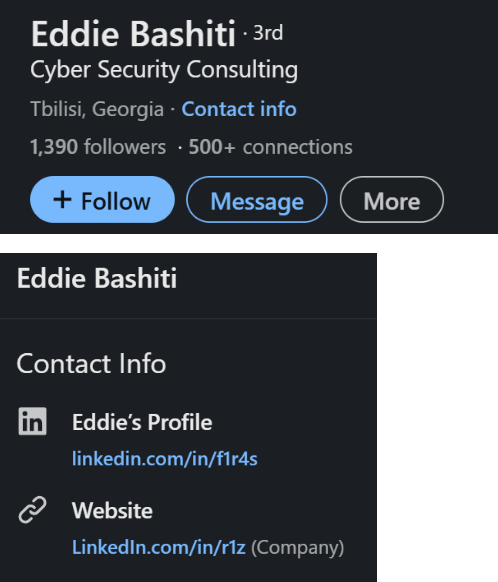
On LinkedIn, he described himself as an Information Technology Architect and consultant, claiming experience in cyber threats, cloud, network, web, and penetration testing. Interestingly, the contact information section included the URL linkedin.con/in/r1z, further connecting his real world identity to his threat actor persona.
Google Maps reviews indicate travel to Russia, along with several reviews in Georgia, consistent with information stating he was based there at the time of his arrest. His most recent review dates back approximately two years. Additionally, his Facebook profile, similar to LinkedIn, listed the name “Eddie Bashiti”, likely used as a nickname or an alternative name to reduce discoverability in relation to his cybercriminal activities. A Youtube profile was also found, featuring mostly hacking related videos.
» Here are the reasons you need cyber threat intelligence
Conclusion
This case highlights how the exposure of threat actors is often driven by consistently poor operational security rather than sophisticated investigative breakthroughs. Despite efforts to compartmentalize his criminal persona, r1z repeatedly reused usernames, images, emails, infrastructure, and communication channels across forums, services, and social media, creating a dense and traceable digital footprint.
KELA identified and tracked this actor years prior by correlating these signals across its data lake, demonstrating that sustained OSINT and underground monitoring can uncover a threat actor’s full digital presence well before law enforcement action, and that even experienced cybercriminals frequently undermine themselves through basic OPSEC failures.
» Ready to begin? Set a FREE session with our experts
FAQs
Who is r1z?
r1z is the online alias of Feras Albashiti, an initial access broker selling compromised network access, hacking tools, and malware.
What did r1z sell?
He sold enterprise network access, EDR-killing malware, and tools like Cobalt Strike to other cybercriminals.
How was r1z caught?
An undercover FBI agent purchased access from him, allowing law enforcement to link his online persona to his real identity.
Which forums did r1z use?
He was active on XSS, Nulled, Altenen, RaidForums, BlackHatWorld, Exploit, and Russian-origin forums.