Threat Actor 303 Exposed: Many Faces, One Hacker
KELA uncovers the many identities of a prolific cybercriminal known as “303,” linking hundreds of forum posts, Telegram accounts, and breaches across continents. The investigation exposes his tactics, regional ties to South America, and a blurred line between hacking and self-promotion.
Published November 3, 2025

KELA’s latest research sheds light on a prolific cybercriminal who has operated under dozens of aliases across the cybercrime underground. Over the past several years, this individual, known variously as “303,” “NetworkBrokers,” “EvilCorp,” “g0d,” and many others, has built a sprawling online presence spanning multiple hacking forums, Telegram channels, and social media accounts. The investigation reveals a tangled mix of genuine hacking, suspected scamming, and relentless self-promotion.
KELA tracked over 497 forum posts tied to the actor on different forums. Since 2023, the actor has claimed responsibility for dozens of breaches and network accesses, including targets in the USA, Japan, Taiwan, Brazil, Argentina, and more.
The full threat actor profile, including exclusive and detailed information not covered in this blog, is available to KELA customers and upon request.
» Get started for free with KELA and strengthen your cybersecurity
From BreachForums to DarkForums
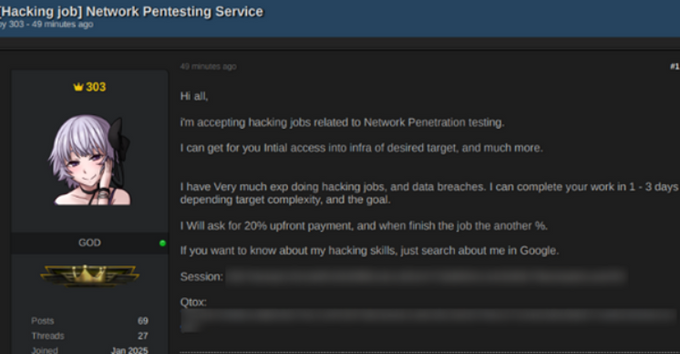
The traces of the investigation start in 2023 on the now-seized BreachForums, one of the most notorious hubs for data leaks and network sales before its seizure by the FBI. There, the actor was using one of his many aliases to advertise data breaches, recruit hackers, and offer network access for sale. He often presented himself as part of a larger group, hinting at affiliations with names like “HaxSec,” “PlayCat,” and “ZeroToleranceGang.”
Over time, he claimed responsibility for breaches affecting entities across multiple continents: governments in Europe, Africa, and South America, telecom providers, educational institutions, and even game developers from Spain. However, KELA’s analysis found that several of these “leaks” were not original at all. Some were recycled from other users’ old posts.
When BreachForums was taken down in early 2025, the actor quickly resurfaced on other forums - DarkForums, Exploit, and PatchedForums, under new identities. There, he continued selling databases, shell access, and remote desktop credentials for targets in Asia, the Middle East, and the United States. He also maintained an active social presence: greeting newcomers, reminding others to follow forum rules, and promoting his hacking services.
» Make sure you understand the most targeted entry points by attackers
Web of Identities and Infrastructure
Across forums, one constant pattern emerged: the same contact details, using the same Telegram ID while changing the usernames tied together all of his personas. Whether appearing as “NetworkBrokers” or “EvilCorp,” he advertised Telegram handles like @threezerothreeSecurity and @supp1995, as well as encrypted email addresses and Jabber accounts.
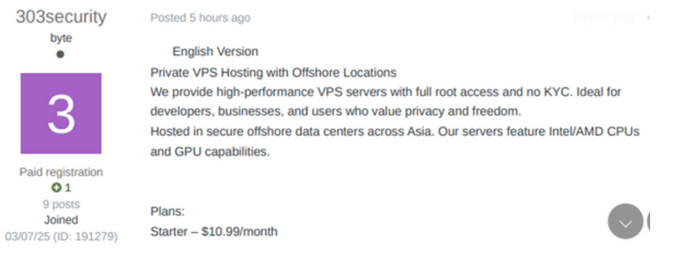
At one point, he launched a website called leaknation[.]st, which he promoted as a VPS rental and “stresser” (DDoS) service. Archive data shows that, before hosting this VPS business, the site briefly functioned as a small hacking forum titled LeakNation, where he operated as an administrator. WHOIS records for the domain listed an alias and a masked email address.
» Learn about the key cyberthreats coming in 2025
OSINT Traces: Connecting the Dots
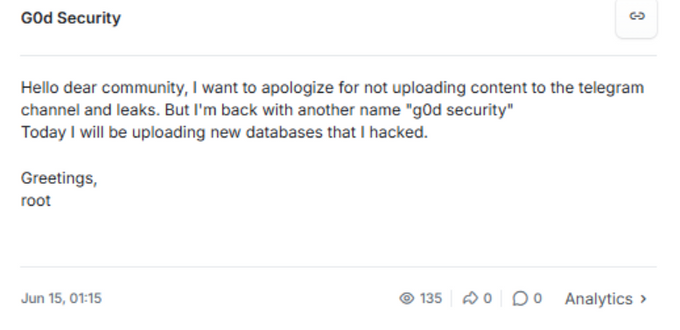
Since 2021, the same Telegram account ID has cycled through more than a dozen usernames, from “ev1ntentually” and “rootkitsecurity” to “traphousemob1” and “threat303.” Through this account, the actor advertised network access sales, discussed hacking tools, and participated in communities focused on credit-card fraud, malware, and cryptocurrency. Interestingly, most of the channels he joined or interacted with were Spanish-speaking, suggesting either fluency in Spanish or ties to a Spanish-speaking country. The actor also ran his own Telegram channel, renamed several times between 2023 and 2024, which he used to promote data leaks and advertise DDoS services.
Outside the cybercrime scene, the actor tried to build a more legitimate image on X, where he ran several accounts that blended hacking boasts with political commentary and occasional references to Uruguayan football clubs. Over time, he linked himself to multiple hacker groups, while portraying himself as a “Blue Teaming” or “Bug Hunter” expert.
On GitHub, the actor maintained several profiles under names such as “g0dsecurity” and “retr0security”. These accounts hosted proof-of-concept exploit code, ransomware samples, and tools labeled as “Raven” and “BlackOut.” The repositories also listed “Hell” as the user’s location, a recurring joke across his profiles.
By cross-referencing usernames, Telegram handles, and GitHub profiles, KELA identified a consistent footprint pointing toward South America, specifically, Uruguay. Multiple IP addresses from the BreachForum leak tied to his forum registrations resolved to the Montevideo area, while timestamps from his GitHub repositories aligned with the GMT-3 timezone used in Argentina and Uruguay.
» Read more: Ransomware groups are selling network access directly
The Search for Credibility
Despite his frequent rebranding, certain behavioral traits stayed constant. The actor was always quick to promote himself, eager to appear connected, and prone to exaggeration. For instance, he frequently claimed ties to high-profile entities like major consulting firms or luxury brands, however, none of which were ever verified. In several cases, KELA found that his “breach” announcements simply copied existing leaks, posted months or years earlier by unrelated actors.
At the same time, he demonstrated a moderate level of operational security. He obscured his real email addresses on social platforms, used encrypted messengers for deals, and diversified contact methods across platforms. However, he also left consistent digital traces, particularly IP data and recurring monikers that exposed his likely origin.
» Discover how Telegram’s new data sharing rules affect cybercriminals
Behind the Persona
KELA’s analysis suggests that the individual behind these many aliases is likely a single actor who has operated continuously since at least 2021. The evidence points to a Spanish-speaking user based in Uruguay. His online behavior combines authentic technical skill with manipulation, as he blends genuine exploits and tools with inflated or recycled leaks to maintain visibility and attract buyers.
The actor’s contradictory conduct - presenting himself as a cybersecurity professional while simultaneously selling stolen data, illustrates a common dynamic in the modern underground. Many such figures straddle both worlds: exploiting technical expertise for both legitimate work and criminal profit.
» Read more: Reasons you need cyber threat intelligence
Unmasking the Patterns That Matter
KELA’s research into “303” highlights how a single, persistent actor can adapt, rebrand, and exploit multiple platforms to maintain visibility and influence within the cybercrime underground. By uncovering the overlaps between his various personas, KELA demonstrates the value of cross-platform intelligence collection and behavioral analysis in attributing malicious activity to specific individuals.
For threat intelligence professionals, these findings illustrate how consistent identifiers, such as Telegram IDs, linguistic patterns, and regional infrastructure, can reveal deeper actor linkages and operational continuity. For law enforcement, the investigation offers potential leads to track the actor’s network, trace infrastructure, and monitor his migration across platforms.
Ultimately, this case serves as a reminder that even actors skilled in deception and rebranding often leave behind digital fingerprints. Identifying and understanding those traces enables both intelligence teams and law enforcement to better anticipate, detect, and disrupt ongoing threat activity.
» Don’t let threat actors take you by surprise. Request a free trial of KELA’s Cyber Threat Intelligence Platform
FAQs
Who is the cybercriminal known as “303” and why is he significant?
“303” is a prolific threat actor who has operated under dozens of aliases across multiple forums, Telegram channels, and social media accounts. He combines genuine hacking with scamming and self-promotion, making him a high-profile figure in the cybercrime underground.
Has “303” been linked to actual breaches or stolen data?
Yes, the actor has claimed responsibility for dozens of breaches targeting organizations in the USA, Japan, Taiwan, Brazil, Argentina, and more.
However, KELA has also identified instances of recycled or exaggerated claims, emphasizing the need for verified intelligence.
What can organizations learn from this actor’s behavior?
Organizations and threat intelligence teams can use this case to understand how persistent actors rebrand, exploit multiple platforms, and leave digital footprints.
Recognizing these patterns helps anticipate attacks, prioritize threats, and take timely protective actions.