Lessons From Okta and Beyond: Protecting Your Company From Compromised Machine Threats
Published February 21, 2024.

Remember the Okta security incident last October? Well, the dust has settled, and the final investigation report is out. But for Cloudflare, the story didn’t end there. A sophisticated attack leveraged a compromised Okta session to gain access to their systems, raising some critical questions about security best practices.
The Incident Unfolded:
- It all started with the Okta compromised in October 2023, during which Cloudflare-related data – such as session tokens – was exposed
- This third-party breach allowed attackers to hijack three Cloudflare service accounts, bypassing even two-factor authentication
- Using the compromised service accounts, the attacker was able to access Cloudflare’s Atlassian Suite and search Confluence, Jira and source code (via Bitbucket) for secrets and hardcoded keys to facilitate lateral movement. According to Cloudflare’s own account, the attacker was discovered and stopped before any further exploitation occurred
Beyond Okta: Why Machines Matter:
While the Okta incident grabbed headlines, let’s not forget that attackers may gain access to your critical business services – like Git services, CRM, ticketing systems or knowledge management platforms – just by exploiting credentials obtained from infected machines within your organization.
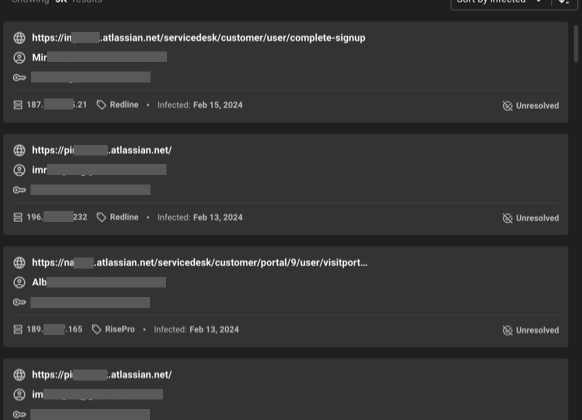
An example for compromised Atlassian accounts as shown in KELA’s Identity Guard
So, What Can You Do?
- Double Down on Authentication: Two-factor authentication is crucial, but it’s not the end-all solution. Consider additional layers like risk-based authentication and endpoint security tools.
- Educate Employees: Exit processes and data handling protocols play a vital role in minimizing potential damage. Ensure employees understand these procedures.
- Embrace Threat Intelligence: Proactive solutions can identify compromised accounts as soon as they appear online, empowering your security team to take quick action before attackers exploit them.
The Okta-Cloudflare incident serves as a stark reminder that security threats evolve and require a multi-layered approach. Combining strong authentication, vigilant employee training, and strong threat intelligence will give you a fighting chance against sophisticated attackers.
Looking for more insights?
- Explore the KELA Research section to understand the latest threats and compromised accounts.
- Subscribe to our mailing list for regular updates and security tips.