Still Hot: 2022 Top Exploited Vulnerabilities Discussed on Cybercrime Sources
Updated August 14, 2023.

In August 2023, the US Cybersecurity and Infrastructure Security Agency (CISA) published a list of the top routinely exploited vulnerabilities in 2022. The list included vulnerabilities disclosed in 2018-2022. While researching recent cybercrime chatter on these vulnerabilities, KELA discovered that the most discussed flaws out of this list include:
- ProxyShell (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) affecting Microsoft Exchange servers
- CVE-2018-13379 affecting Fortinet FortiOS
- Follina (CVE-2022-30190) affecting Microsoft Support Diagnostic Tool
In this blog, KELA summarizes how threat actors share tips and tools for finding and exploiting vulnerable instances, sell access to corporate networks affected by the flaws and bypass patches.
ProxyShell (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207)
Summary: ProxyShell is a sophisticated attack that chains three Microsoft Exchange vulnerabilities: CVE-2021-34473 (Pre-auth Path Confusion leads to ACL Bypass), CVE-2021-34523 (Elevation of Privilege on Exchange PowerShell Backend), CVE-2021-31207 – (Post-auth Arbitrary-File-Write leads to RCE). Chaining these three vulnerabilities allows an attacker to achieve remote code execution on a target machine by impersonating an arbitrary user, bypassing authentication, and writing an arbitrary file.
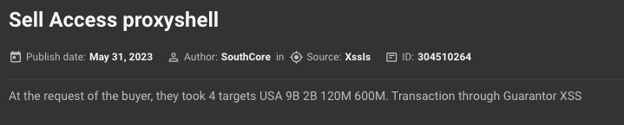
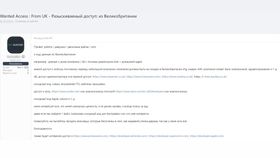
Cybercrime chatter: More than two years after the patch date, ProxyShell still appears to be widely discussed by threat actors and used in different campaigns. For example, in May 2023, a threat actor started a thread where they sell access to corporate Microsoft Exchange servers vulnerable to ProxyShell. The actor claimed the servers belonged to companies from the US, Canada, Australia, the UK, Germany, and others, with revenue from USD 5 million to USD 9 billion. Over the next two months, the actor regularly updated the thread to sell access to around 2000 networks. In parallel, the actor has also sold some networks one by one:
Auto-translated by KELA platform
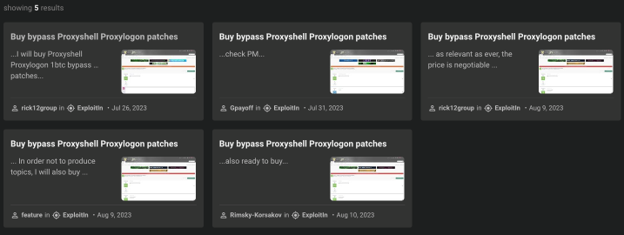
The same actor claimed they have found a way to bypass a patch for ProxyShell and will provide instructions to buyers. They have also offered to buy the bypass separately. In parallel, multiple users on another forum were looking for a bypass, for which they were ready to pay up to 1 BTC:
Auto-translated by KELA platform
Based on other discussions, threat actors use Shodan and Masscan tools to discover potential targets. The existence of bypass suggests that enterprise defenders should not rely only on patching their systems, but also implement a complex strategy to avoid being compromised through the use of ProxyShell.
CVE-2018-13379
Summary: CVE-2018-13379 is a critical vulnerability that affects Fortinet FortiOS multiple versions (FortiOS 6.0 – 6.0.0 to 6.0.4; FortiOS 5.6 – 5.6.3 to 5.6.7; FortiOS 5.4 – 5.4.6 to 5.4.12). The vulnerability allows an attacker to target the Fortinet SSL VPN web portal, granting them the ability to bypass authentication and gain unauthorized access to the internal network resources. Exploiting CVE-2018-13379 involves an attacker sending a specially crafted HTTP request to the targeted Fortinet SSL VPN web portal. This request, when processed, can enable the attacker to retrieve arbitrary files from the system.
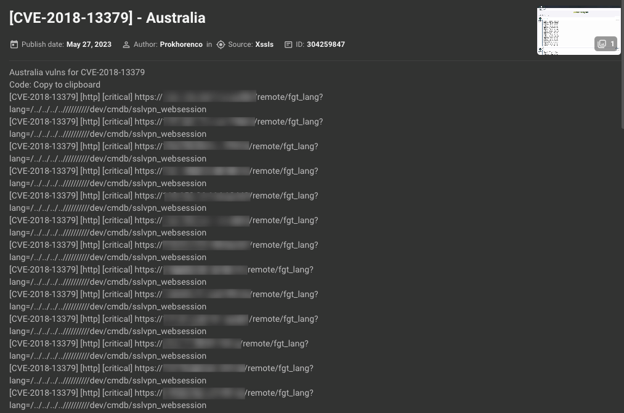
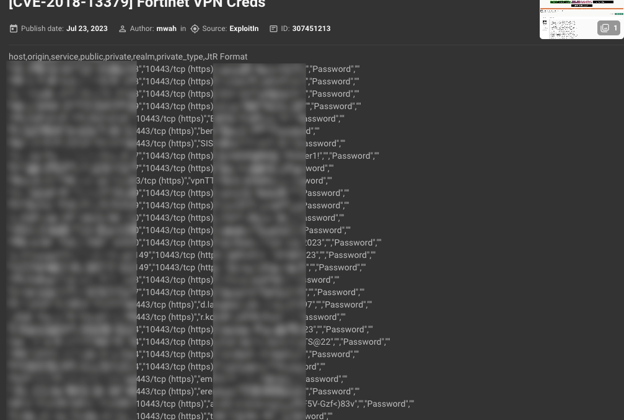
Cybercrime chatter: KELA has seen multiple threat actors exploiting this vulnerability over the years — for many Initial Access Brokers, for example, it’s one of the favorite ways of obtaining credentials. Despite the fix being available for a few years now, many devices are still unpatched, as can be seen from potential target lists shared by users on cybercrime forums on a monthly basis. Some users share only information for further exploitation, while others post the output with already obtained credentials:
When asked why to share this information for free, one of the users answered: “It allows others who dont have much experience to learn how to hack business networks through their VPNs following a guide like the Bassterlord Networking Manual [a step-to-step guide on compromising corporate networks written by an actor known as Bassterlod – KELA]. Also shows you how you can go out and scan for the vulnerabilities yourself.” In other posts, the same actor has shared a manual for scanning IP ranges using Masscan and vulnerabilities using Nuclei.
As more actors are getting handy in exploiting this vulnerability, the threat remains, therefore ensuring patching CVE-2018-13379 on all instances is critical.
Follina (CVE-2022-30190)
Summary: CVE-2022-3019 is a remote code execution vulnerability in Microsoft Support Diagnostic Tool (MSDT) in Windows, dubbed “Follina”. The flaw is triggered when MSDT is called using the URL protocol from a calling application such as Word. Follina requires minimal user interaction to achieve payload execution, such as opening a malicious document. Attackers exploiting this bug could gain users’ privileges, install programs, view, change, or delete data and create new accounts.
Cybercrime chatter: Follina is the vulnerability that requires threat actors to be creative in finding ways to trick a user into opening a malicious document. Logically, some of the discussions on cybercrime forums are related to social engineering methods. Particularly interesting are cases where Follina is exploited following an earlier compromise.
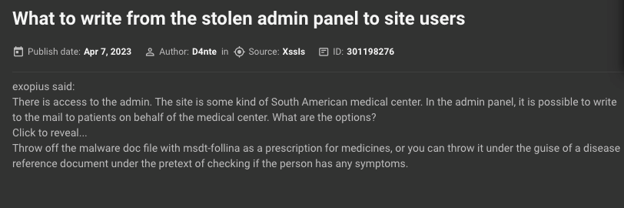
For example, in April 2023 a user wondered what is the best way to abuse access to the admin panel of a South American medical center they obtained. They specified that sending emails to the center’s patients is possible through this panel. Then, another user suggested sending a malicious document designed to exploit Follina under the disguise of a medical prescription.
Auto-translated by KELA platform
Though Follina does require user interaction, it is a minimal one, and therefore patching the flaw should still be treated as a priority. On cybercrime forums, multiple guides on exploiting Follina are available, expanding the number of threat actors that may choose this method to start or further advance their attacks.
Conclusion
Cybercrime chatter adds context to information about disclosed vulnerabilities and provides valuable insights into emerging threats, helping companies take proactive measures to defend against attacks, and contributing to overall cybersecurity awareness and preparedness. KELA recommends using this information for:
- Prioritization of patching and mitigation efforts. Tracking discussions on cybercrime forums allows a company to stay informed about the latest vulnerabilities being targeted by attackers and apply patches in a timely manner.
- Risk assessment. Understanding which vulnerabilities are actively being discussed on cybercrime forums enables a company to assess its risk exposure and make informed decisions about allocating resources to address the most critical vulnerabilities.
- Proactive defense against real attack techniques. Monitoring these forums provides insights into the methods and tools that cybercriminals are using to exploit vulnerabilities. This information can be used to fine-tune defensive strategies and train security personnel.
- Incident response planning. If a company knows about vulnerabilities that are actively being exploited or discussed, it can develop targeted incident response plans. This ensures that they’re prepared to react swiftly and effectively if an attack occurs.
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.