What Is Cyber Threat Intelligence? A Practical Approach to Security
Cyber threat intelligence is a necessity for organizations looking to effectively defend against today's sophisticated cyber threats. By harnessing the power of CTI, organizations can move from a reactive to a proactive security posture.
Updated May 25, 2025

In today's interconnected world, organizations of all sizes face a constant barrage of cyberattacks, from phishing emails and ransomware to sophisticated intrusions aimed at stealing valuable data. In fact, we observed over 4.3 million machines infected globally by infostealer malware in 2024.
Cybercriminals are always evolving—and staying ahead of these changing threats requires more than just reactive security measures. This is where cyber threat intelligence (CTI) comes into play, providing organizations with the knowledge they need to proactively defend against attacks, minimize damage, and improve their overall security posture.
» Skip to the solution: Try KELA's cyber threat intelligence for free
What Is Cyber Threat Intelligence?
Cyber threat intelligence (CTI) is the process of collecting, analyzing and sharing information about cyber threats, helping to make strategic and operational decisions. It provides valuable, contextualized insights for security teams to proactively stop impending attacks.
Unlike traditional security measures that focus on internal defense, CTI is outward-looking and proactive, emphasizing the identification, understanding, and mitigation of external threats before they materialize. It enables security teams to make well-informed decisions based on real-time intelligence, enhancing their ability to anticipate, prevent, and respond to cyber incidents effectively.
Why Is Cyber Threat Intelligence Important?
Cybercriminals are advancing rapidly, leveraging phishing, data leaks, infostealers and ransomware, to steal sensitive data. In 2024 alone, our cybercrime report highlighted 330 million compromised credentials and 3.9 billion shared in the form of credentials lists sourced from infostealer logs.
Attackers exploit vulnerabilities quickly—new CVEs surface in underground forums within weeks, while AI-powered threats now include deepfakes, backdoored AI models, and adversarial attacks on AI-integrated platforms and large language models like ChatGPT.
Traditional security measures detect and respond to attacks after they occur, but this isn't enough to handle the rapidly-evolving nature of cyber threats. CTI enables a proactive approach that monitors compromised assets, services, and identities in real-time, helping organizations prevent unauthorized access before a breach occurs.
Strengthening Cyber Defenses With Intelligence-Driven Security
Access to intelligence on threat actor tactics and behaviors helps security teams with threat hunting, predicting attacks and prioritizing risk mitigation efforts, stopping threats before they escalate. Proactive monitoring of compromised assets and emerging attack methods helps security teams stay ahead of adversaries.
Advantages include:
- Prevention: Identify and mitigate threats before they escalate.
- Visibility: Gain real-time insights into emerging cyber risks and a view from the attacker's perspective.
- Resilience: Strengthen defenses against ransomware, data leaks, and targeted attacks.
» Not convinced? Here are more reasons you need cyber threat intelligence
The Key Components of CTI
1. Data Collection: Intelligence From the Underground
CTI gathers intelligence from multiple sources including:
- External attack surface discovery
- Dark web marketplaces and underground forums
- Hacking discussions on private messaging apps
- Phishing domains and fake social accounts
- Software supply chain
Cybercriminals trade stolen credentials, network access, and payment details, making continuous monitoring essential. Infostealer malware and ransomware groups facilitate and source these underground channels to monetize stolen data. Tracking these sources helps organizations identify and mitigate exposure before it leads to a breach.
2. Analysis & Contextualization: Turning Data Into Actionable Intelligence
Raw data alone is not enough; it must be analyzed and contextualized. Security teams correlate malware logs, credential dumps, and attack trends to filter real threats from noise.
Understanding tactics, techniques, and procedures (TTPs) allows organizations to anticipate attack methods and prioritize responses. This process helps identify high-risk vulnerabilities and assess the likelihood of exploitation.
3. Operationalization: Integrating CTI Into Security Workflows
For CTI to be effective, it must be seamlessly integrated into SOC operations, SIEM systems, and incident response workflows. Automation enhances real-time detection, malicious domain blocking, and compromised identities and assets flagging.
Organizations using CTI for vulnerability management can proactively patch high-risk flaws before they are exploited. A well-integrated CTI strategy enables security teams to detect, respond to, and prevent attacks more efficiently.
Different Types of Cyber Threat Intelligence
CTI is categorized into four types: strategic, tactical, operational, and technical intelligence. Each type serves a distinct role in cybersecurity, from informing executive decisions to detecting real-time threats.
1. Strategic Intelligence: High-Level, Long-Term Threat Trends
Strategic intelligence provides big-picture insights into the evolving threat landscape, helping executives, CISOs, and decision-makers make informed security strategies. Instead of focusing on individual attacks, it focuses on:
- Long-term trends
- Geopolitical cyber threats
- Industry-specific risks
By analyzing nation-state cyber activities, ransomware group tactics, and underground market shifts, organizations can anticipate risks and allocate security investments effectively.
2. Tactical Intelligence: Understanding Attacker TTPs
Security teams leverage this intelligence to enhance detection capabilities, improve defenses, and refine response strategies. Understanding how attackers operate—whether through phishing campaigns, social engineering, or zero-day exploits—enables security teams to develop an effective threat hunting program that countermeasures and disrupts adversarial methods before they succeed.
3. Operational Intelligence: Real-Time Threat Insights
Operational intelligence delivers real-time, actionable insights into active cyber threats, ongoing attacks, and imminent risks. This intelligence is essential for SOC analysts, incident response teams, and threat hunters, providing visibility into attacker infrastructure, emerging malware campaigns, and compromised identities and assets.
With this knowledge, security teams can respond swiftly, block malicious domains, and prevent threats from escalating.
4. Technical Intelligence: Indicators of Compromise (IOCs)
Technical intelligence focuses on specific artifacts of cyber threats, such as malware hashes, IP addresses, domain names, and leaked credentials. This data feeds directly into firewalls, SIEM systems, and threat intelligence platforms to automate threat detection and response.
Monitoring IOCs from underground forums, malware logs, and breach dumps helps security teams identify threats before they infiltrate networks, strengthening overall defense mechanisms.
How CTI Helps Security Teams
SOC Teams
CTI significantly improves threat detection accuracy by providing up-to-date information on emerging threats, tactics, techniques, and procedures (TTPs) used by threat actors. This enables Security Operations Center (SOC) teams to fine-tune their detection rules and signatures, reducing false positives and focusing on genuine threats.
CTI dramatically accelerates incident response times by providing context and actionable intelligence, allowing analysts to quickly understand the nature of an attack and take appropriate countermeasures.
» Learn more: Benefits of automating CTI into SOC activities
Incident Response Teams
During an incident, CTI provides crucial context, revealing the attacker's identity, motivations, and the tools and methods employed. This information enables incident responders to understand the scope and severity of the attack, prioritize remediation efforts, and develop effective mitigation strategies.
Risk Management Teams
CTI plays a key role in identifying and assessing potential risks by providing insights into vulnerabilities, threat actor activity, and emerging threats. This helps organizations identify potentially compromised assets, assess the risks associated with third-party vendors, and prioritize security investments.
By proactively identifying and mitigating risks, organizations can strengthen their overall security posture and reduce their attack surface.
Fraud Prevention & Brand Protection Teams
CTI is essential for detecting and preventing fraud by identifying indicators of malicious activity, such as data leaks, phishing domains, and impersonation attacks. By monitoring for these threats, organizations can take proactive steps to protect their customers and their brand reputation.
CTI allows security teams to detect fraudulent activity before it causes significant damage, minimizing financial losses and reputational harm.
Practical Applications of CTI in Cybersecurity
1. Identifying Malicious Activity
CTI techniques improve the effectiveness of internal security architectures to block attacks or access to malicious Command and Control (C2) by monitoring connection attempts to the following:
- Malicious IP addresses
- Domains
- URLs
- Hashes
- Network traffic analysis (PCAP)
- JA3
- JARM
2. Preventing Data Theft
CTI can help with remediation, identifying compromised systems, and assisting in the discovery of indicators of compromise (IOCs), potentially correlating with previously-identified malicious campaigns and possible threat actors.
CTI also assists incident response teams by providing useful information that can speed up the response to important events, providing context on data and security information. For example, the identification of data leaks from suppliers in the supply chain that could affect customers.
» Here are the most targeted entry points by hackers
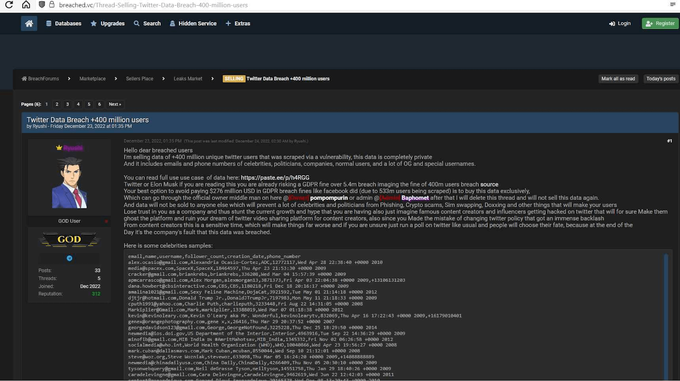
The 2022 Twitter data breach that affected over 400 million users is a great example of the data theft that could be prevented by CTI.
3. Mitigating Phishing Attacks
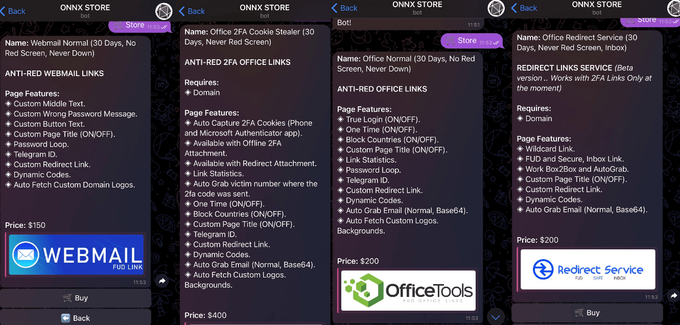
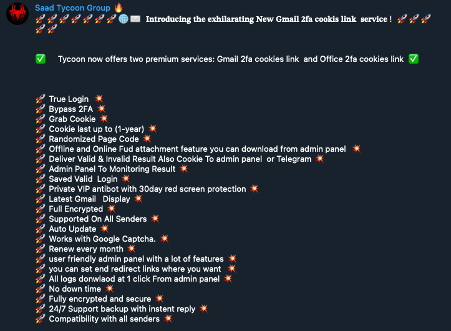
Cybercriminals have been perfecting their attack techniques and tools in newly identified campaigns. In fact, there are now phishing as a service platforms like ONNX Store and Tycoon that use social engineering techniques to steal data and obtain unauthorized access to security systems, then sell the information to malicious individuals. These platforms are highly lucrative for threat actors.
One of the possible mitigations against phishing emails is personalized cyber awareness training and regular phishing simulations that educate employees to not open suspicious emails and to report them to security.
» Learn more: How to prevent phishing attacks
4. Strengthening Financial Services
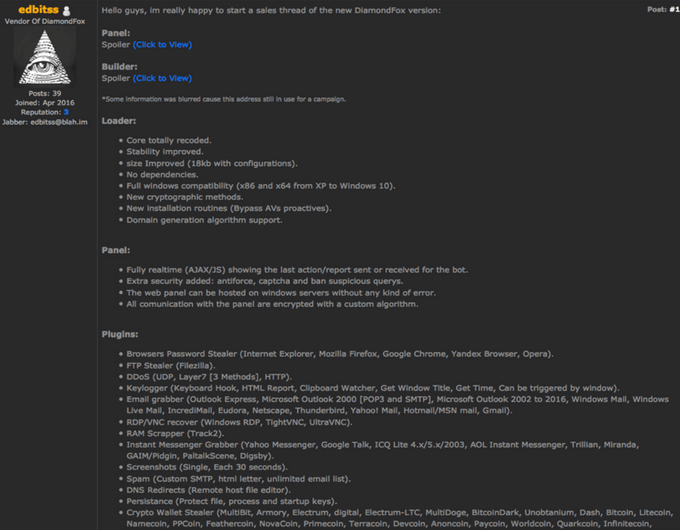
The financial sector should focus on threats targeting financial assets, such as point-of-sale (POS) malware, phishing attacks, and infostealer malware such as DiamondFox or Lumma. CTI can act by monitoring threats that may arise from suppliers, partners, and service providers.
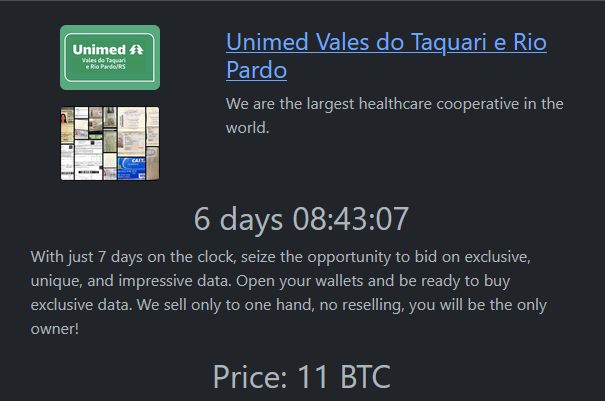
5. Protecting Healthcare Records
The healthcare sector is considered particularly vulnerable to malicious activity targeting confidential patient data, such as electronic health records (EHRs).
CTI can alert hospitals to ransomware attacks targeting EHRs, allowing them to patch vulnerabilities and strengthen their defenses before an attack occurs. It can also help identify and prevent data breaches involving sensitive patient information.
» See how ransomware and extortion actors are collaborating
6. Automating Vulnerability Management
Threat intelligence platforms can automatically analyze and prioritize threat data, reducing the manual effort required by security analysts. Automated playbooks can be triggered based on CTI alerts, automatically containing threats and mitigating their impact.
If CTI reveals that a specific vulnerability in a commonly used software library is being actively exploited, organizations can prioritize patching that vulnerability to reduce their risk. Additionally, CTI can inform risk assessments by providing insights into the likelihood and potential impact of different cyber threats, assisting organizations in focusing their resources on the most critical risks.
» Make sure you understand how threat actors breach and exploit your data
7. Facilitating Collaboration and Information Sharing
Information sharing and analysis centers (ISACs) and information sharing and analysis organizations (ISAOs) facilitate the sharing of threat intelligence between organizations in the same industry, allowing them to collectively improve their defenses. For example, if one bank identifies a new phishing campaign, they can share that information with other banks through their ISAC.
Real-World Examples of CTI in Action
Example 1: Preventing Ransomware Attacks
CTI platforms often track the evolution of ransomware groups, including their preferred TTPs, infrastructure, and targets. By analyzing these patterns, organizations can proactively implement security controls to mitigate the risk of ransomware infection.
For example, threat intelligence providers like KELA share indicators of compromise (IOCs) related to known ransomware campaigns such as Anubis, allowing organizations to block malicious IP addresses, domains, and file hashes.
» See our complete guide to combating ransomware
Example 2: Identifying and Stopping a Supply Chain Attack
The SolarWinds supply chain attack demonstrated the devastating impact of compromised software updates, resulting in over 18,000 SolarWinds customers installing updates containing malicious code that hackers used to steal customer data and spy on other organizations.
CTI played a vital role in investigating the attack and identifying the threat actors involved. Security vendors like Microsoft and FireEye (now Mandiant) provided detailed analysis of the attack, including the TTPs used by the threat actors. These investigations relied heavily on CTI to track the attackers' infrastructure, identify compromised systems, and develop mitigation strategies.
» Dive deeper with our guide to navigating third-party risks
Example 3: Tracking and Taking Down an Underground Cybercriminal Operation
Law enforcement agencies and security researchers use CTI to track and disrupt underground cybercriminal operations. Intelligence about dark web marketplaces, forums, and criminal groups allows for proactive disruption of criminal activity.
For example, the takedown of the Emotet botnet involved a collaborative effort between law enforcement agencies and security researchers from multiple countries. CTI was used to track the botnet's infrastructure, identify its command-and-control servers, and develop strategies for disrupting its operations.
Limitations and Challenges of Cyber Threat Intelligence
- Limited scope: It is impossible to collect intelligence on all existing threats. CTI must focus on the most relevant threats and those that can bring the most benefits to organizations, potentially resulting in smaller threats still causing measurable harm.
- Noise vs. actionable intelligence: CTI can generate a large volume of information, which can make it difficult to identify and prioritize the most relevant threats. Information overload can occur, leading analysts to ignore important alerts, and intelligence analysis can be influenced by bias and subjectivity. Not all data is created equal, and distinguishing between noise and actionable intelligence is a significant challenge.
- Varying data quality: The quality of intelligence depends on the quality of the data used, and incorrect or incomplete data can lead to incorrect analysis. In addition, the labeling of data for supervised learning can be subjective and inconsistent, affecting the quality of AI models.
- Investments in time and cost: Implementing a CTI program requires investment in qualified personnel, tools, and technology. Significant planning is required to allocate resources effectively.
- Complex integrations: Integrating CTI with existing security systems, such as security information and event management (SIEM) and security orchestration, automation, and response (SOAR) systems, can be complex and challenging. Compatibility between different systems and platforms is a crucial factor to consider.
- Gaps in skill: Analyzing and applying CTI effectively requires specialized skills and expertise. Organizations often face a shortage of qualified personnel with the necessary knowledge of threat actor tactics, malware analysis, and intelligence analysis methodologies
Future of Cyber Threat Intelligence
The landscape of cyber threats is constantly evolving along with the field of cyber threat intelligence. Here are some of the key trends shaping the future of CTI:
AI & Machine Learning
Artificial intelligence (AI) and machine learning (ML) are poised to revolutionize CTI by automating the analysis of vast amounts of threat data. ML algorithms can identify patterns and anomalies that human analysts might miss, improving threat detection accuracy and speed.
AI-powered CTI platforms can automate tasks such as malware analysis, vulnerability scanning, and threat attribution, freeing up analysts to focus on more strategic initiatives.
Threat Intelligence Sharing
Increased collaboration and information sharing between governments, enterprises, and Managed Security Service Providers (MSSPs) will be essential for effective cyber defense.
Threat intelligence sharing platforms and initiatives will enable organizations to pool their resources and knowledge, creating a more comprehensive view of the threat landscape.
This collaborative approach, along with the increased standardization of threat information, will help organizations stay ahead of emerging threats and respond more effectively to attacks.
» Here are some reasons MSSPs should embrace CTI
Rise of Cybercrime-as-a-Service (CaaS)
The proliferation of Cybercrime-as-a-Service (CaaS) platforms has lowered the barrier to entry for cybercriminals, enabling even novice attackers to launch sophisticated attacks.
CaaS platforms provide access to a wide range of malicious tools and services, including:
- Ransomware
- Phishing kits
- DDoS attacks
This trend makes CTI more crucial than ever, as organizations need to monitor and defend against a growing number of threat actors and attack vectors. CTI will be vital in tracking these CaaS providers and the threat actors that utilize them.
» Concerned about the future? See these other trends shaping the future of CTI or check out our future of cybercrime podcast
Boost Your Cybersecurity With Cyber Threat Intelligence Today
Cyber threat intelligence is a necessity for organizations looking to effectively defend against today's sophisticated cyber threats. By harnessing the power of CTI, organizations can move from a reactive to a proactive security posture, anticipating and mitigating attacks before they can cause significant damage. From preventing malware infections and phishing attacks to improving vulnerability management and incident response, the practical applications of CTI are vast and impactful.
Thankfully, it doesn't have to be a difficult process. KELA provides a platform that broadens the visibility of threats in contexts uncommon for other cybersecurity areas. We identify credential leaks and monitor a large volume of Deep/Dark Web forums to anticipate and identify the key cybersecurity risks you might face, streamlining all the info in our Threat Actors Hub.
» Ready to get started? Contact us to learn more about our cyber threat intelligence services